About the Security Center (Alpha)
This topic provides an overview of the Replicated Security Center.
The Security Center is Alpha. To get access to the Security Center, reach out to your Replicated account representative.
Overview
The Security Center helps you strengthen security enablement in your application delivery process by making it easier for both you and your enterprise customers to monitor security risks, assess known vulnerabilities, and view security information for each application release.
The Security Center surfaces the results of image scans in both the Vendor Portal and the Enterprise Portal so that your customers can see the same security information that you do for each application version. This results in greater transparency, reduced security questionnaire burden, and the adoption of newer, more secure versions of your application.
Additionally, if there is an update to any image digests associated with an existing release, the Security Center automatically regenerates the SBOM for the relevant release version, which updates calculated CVEs as well. This means that it is not necessary to promote a new release in the Replicated Platform to get an up-to-date SBOM or CVE report in the Security Center.
What Images Are Scanned and Cataloged?
When you promote a release in the Replicated Platform, Replicated identifies all container images that are referenced in the release. The Security Center then automatically generates comprehensive security information for all container images in that release.
The following describes the types of images that Replicated identifies for each release:
- Container images in PodSpecs: Any images defined in your Kubernetes manifests, such as Deployments, StatefulSets, DaemonSets, and so on. To build the list of container images for any Helm charts in the release, Replicated runs
helm templateusing the chart's default values (or, using the Helm values that you provide in the Replicated HelmChart custom resourcebuilderkey). Then, Replicated parses the output ofhelm templateto generate the list of images for the chart. For more information, see Requirements on this page. - Additional images: Any images listed in the Replicated Application custom resource
additionalImagesfield. For example, applications packaged as Kubernetes Operators might need to include additional images that are not referenced until runtime. - Embedded Cluster images: Any infrastructure images used by Replicated Embedded Cluster installations, if relevant.
How CVE Scanning Works
The Security Center is powered by Replicated's SecureBuild technology. With SecureBuild, every image is scanned continuously (not just at release time) using the open source vulnerability scanner Grype. This means that, as new CVEs are disclosed, they automatically appear in your Security Center without requiring a new release.
The following describes the Security Center CVE scanning process:
- For each image that Replicated identified in the release, SecureBuild pulls the image by digest and scans it with Grype. SecureBuild scans for multiple architectures (amd64 and arm64) when relevant.
- Grype compares packages in the image against vulnerability databases, including NVD, OS-specific databases, and language-specific sources.
- Security Center aggregates the vulnerability counts for all images by severity: Critical, High, Medium, and Low.
- For each CVE, Security Center includes an identifier, description, CVSS score, affected artifacts, and available fixes.
- Security Center displays the results of the CVE scan in the Vendor Portal and Enterprise Portal:
- Vendor Portal: In the Vendor Portal, you can view a vulnerability overview with a severity breakdown, top risks, a complete image inventory with CVE counts, and detailed CVE information per image.
- Enterprise Portal: In the Enterprise Portal, your customers can view CVE reports showing known vulnerabilities, per-image details, and CVE reduction metrics when comparing versions.
How SBOM Generation Works
Replicated generates Software Bills of Materials using Syft, an open-source SBOM generation tool from Anchore. SBOMs are created in the industry-standard SPDX JSON format, which satisfies most compliance and security audit requirements. The SBOM includes detailed component information necessary for supply chain security, compliance reporting, and license auditing.
The following describes the Security Center SBOM generation process:
- For each image that Replicated identified in the release, SecureBuild runs Syft to catalog all software components.
- Syft analyzes the image layers and extracts package information from various sources, such as OS packages, language-specific manifests like package.json, go.mod, requirements.txt, and more. The output is a comprehensive SPDX document listing every software component, version, license, and relationship.
- Security Center generates SBOMs for multiple architectures (amd64 and arm64) when available.
- Security Center stores and serves the generated SBOMs through the Replicated Vendor API to make them available for download. Users can download SBOMs from the Vendor Portal or Enterprise Portal:
- Vendor Portal: In the Vendor Portal, you can download SBOMs in SPDX format for a specific release at Releases > [Release Version] > Security.
- Enterprise Portal: Your customers can download release-specific SBOMs in SPDX format from the Enterprise Portal's Security tab.
Requirements
-
Access to the Security Center Alpha requires a feature flag be turned on for your team. For more information, reach out to your Replicated account representative.
-
Version 1.9.0 or later of the Replicated SDK is required to report CVE information from specific customer instances back to the Vendor Portal. For more information, see Customer-Specific CVE Information below.
- For Helm CLI installations, additionally set the Replicated SDK to Report All Images. This ensures that the Security Center reports all container images observed in the cluster. This settting is enabled by default for Embedded Cluster installations.
-
Each Helm chart in the release must have a unique HelmChart custom resource. The HelmChart custom resource is required for both Embedded Cluster and Helm CLI installations in online (internet-connected) or air-gapped environments to create the list of images that are scanned and reported on in the Security Center.
noteFor Embedded Cluster and air gap installations, you do not need to make any changes to your existing HelmChart custom resource(s) to support Security Center image scanning.
For Helm CLI installations in online environments, note that only the HelmChart
chart.nameandchart.chartVersionfields are required to support Security Center image scanning for the given chart. For example:apiVersion: kots.io/v1beta2
kind: HelmChart
metadata:
name: examplechart
spec:
chart:
# name must match the name of the chart
name: examplechart
# chartVersion must match the version of the chart
chartVersion: 1.0.0
Limitations
-
The Security Center is Alpha. The features and functionality of the Security Center are subject to change.
-
Security Center reporting is available only for Embedded Cluster and Helm CLI installations. It is not available for kURL installations or for KOTS installations in an existing cluster.
-
If you have configured the
builderkey in any of the HelmChart custom resources in your release, note that the Security Center uses the Helm values provided in thebuilderkey to create the list of images that are scanned and reported on for the given Helm chart. The Security Center will scan and report on this same list of images for both air gap and online installations. If there are any images that you want reported on in the Security Center, ensure that they are exposed by the values provided in thebuilderkey.
Vendor Portal Security Center Interfaces
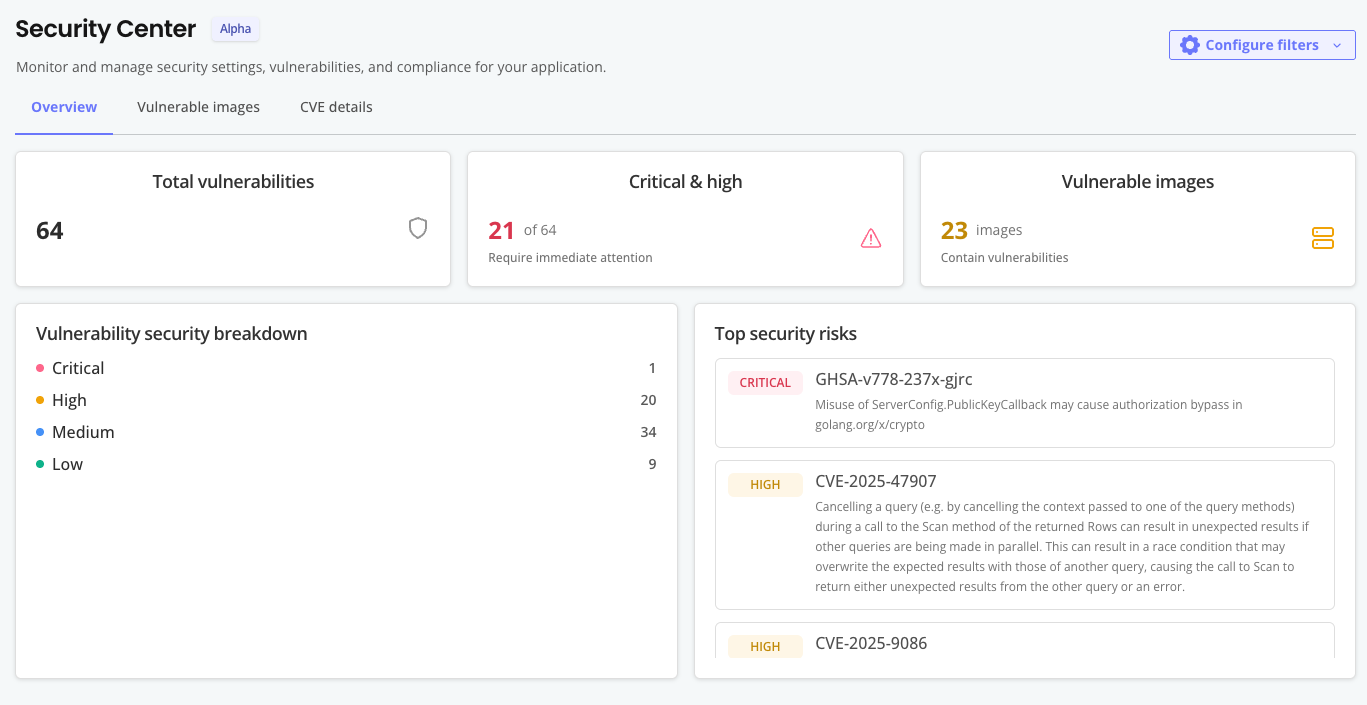
Security Center Dashboard
The Security Center dashboard is available in the Vendor Portal at [App name] > Security.
The following shows an example of the Security Center dashboard:
View a larger version of this image
You can filter for the information on the Security Center dashboard by release type (Linux/Embedded Cluster or Helm) and release channel. The information displayed on the Security Center dashboard applies to the currently promoted release of the selected type on the selected channel.
The Security Center dashboard includes the following:
- An overview of vulnerabilities present in the release, including a breakdown of CVE severity (Critical, High, Medium, Low) and a detailed list of the top security risks
- On the Container images tab, a complete list of scanned images with vulnerability counts per image
- On the CVE details tab, for each CVE identified:
- The CVE identifier and description
- The CVSS score and severity rating
- A list of images affected by the CVE
- Fixed versions (when available)
Release-Specific CVE Information
CVE details are available for all current and previously promoted application release versions. To view CVE information for a specifc release, go to Releases > [Release Version] > Security.
Customer-Specific CVE Information
You can view CVE details at the customer level for active instances running the Replicated SDK verson 1.9.0 or later. This gives you visibility into all container images running alongside your application, helping you identify security risks and urgent upgrade needs across your customer base.
To view CVE information for a specific customer instance go to Customers > [Customer] > [Instance] > Security.
Enterprise Portal Security Center Interface
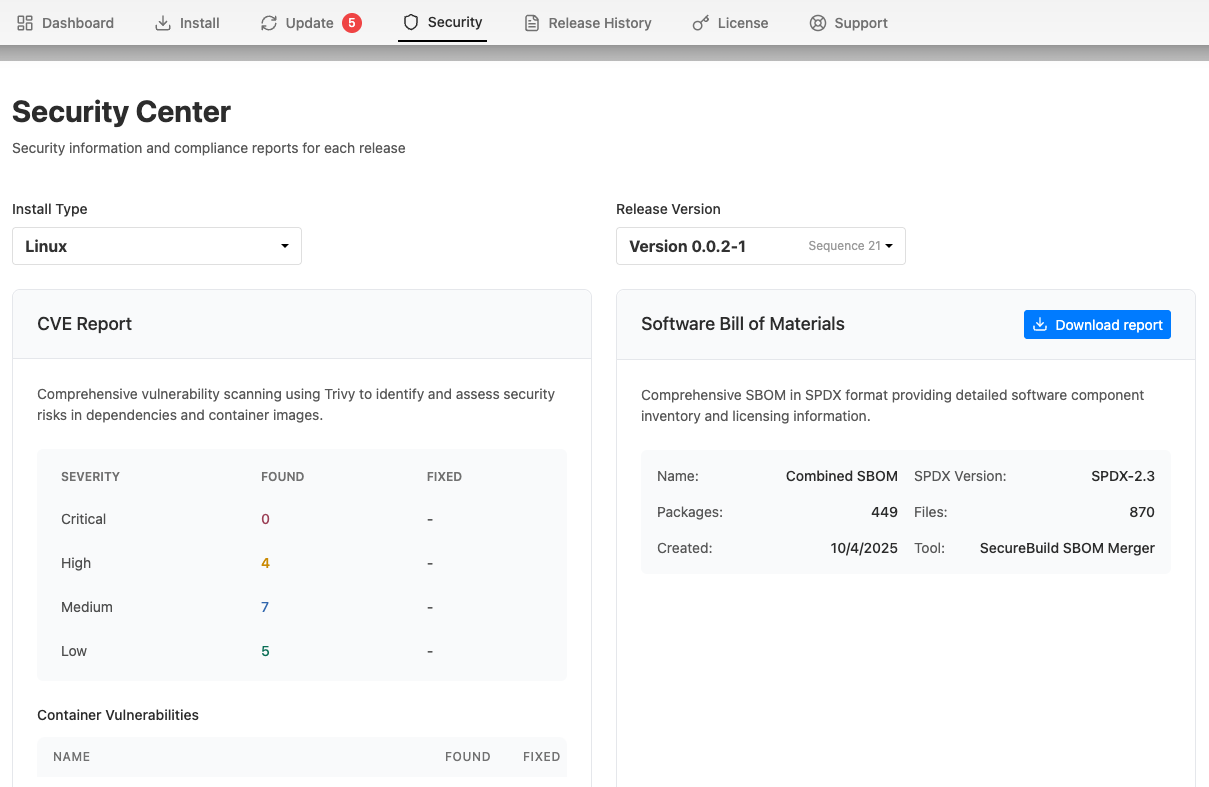
The Enterprise Portal Security Center allows you to provide key security information to your enterprise customers alongside your application releases.
The Security Center tab of the Enterprise Portal is not enabled by default. See Enable the Enterprise Portal Security Center. When enabled, the Security Center intelligently filters data based on the customer's installation type, ensuring that customers only see relevant security information.
On the Security Center tab of the Enterprise Portal, for each available release version, customers can:
- View a CVE report with the complete list of known vulnerabilities and their severity levels
- View details about the vulnerabilities identified for each image
- Understand how many CVEs are fixed by upgrading to newer versions
- Download the Software Bill of Materials (SBOM) in SPDX format for compliance and security audits
The following shows an example of the Security Center dashboard in the Enterprise Portal:
View a larger version of this image
Enable the Enterprise Portal Security Center
The Security Center tab in the Enterprise Portal is not enabled by default. If the Security Center feature flag is enabled for your Vendor Portal team, you can optionally enable the Enterprise Portal Security Center tab on a per-customer basis or globally for all customers.
To enable the Security Center tab in a customer's Enterprise Portal, go to Customers > [Customer] > Enterprise Portal access.
To enable the Security Center tab for all customers using the Enterprise Portal, go to Enterprise Portal > Portal Settings > Optional Features and enable the Enable Security Center feature toggle.
Include and Exclude Images From Security Center Scans
You can explicitly include or exclude images from being scanned by the Security Center:
-
To exclude images from being scanned in Helm CLI installations, use the installer-only annotation. This is useful if your application has any charts and resources that are only relevant to Embedded Cluster installations and should not be shown to customers that install with the Helm CLI.
-
If there are any images that are not referenced in the PodSpecs for your application but should be included in Security Center image scans, list those images in the Application custom resource additionalImages field.